- Cryptography is the study of securing communications from outside observers.
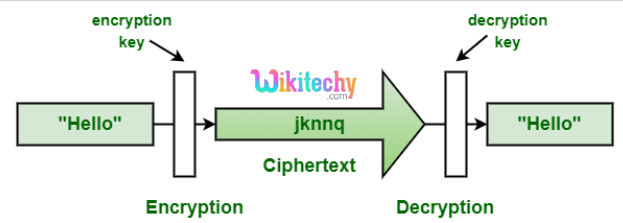
- Encryption algorithms take the original message, or plaintext, and converts it into ciphertext, which is not understandable.
- The key allows the user to decrypt the message, thus ensuring on they can read the message.
- The strength of the randomness of an encryption is also studied, which makes it harder for anyone to guess the key or input of the algorithm.
- Cryptography is how we can achieve more secure and robust connections to elevate our privacy.
- Advancements in cryptography makes it harder to break encryptions so that encrypted files, folders, or network connections are only accessible to authorized users.
Objectives of Cryptography:
- Confidentiality: Confidentiality guarantees that only the supposed recipient can decrypt the message and study its contents.
- Non-repudiation: Non-repudiation means the sender of the message cannot back down in the future and deny their reasons for sending or creating the message.
- Integrity: Integrity focuses on the ability to be sure that the data contained in the message can’t be changed at the same time as in storage or transit.
- Authenticity: Authenticity ensures the sender and recipient can confirm every other’s identities and the destination of the message.
Types of Cryptography
- Secret Key Cryptography
- Public Key Cryptography
- Hash Functions

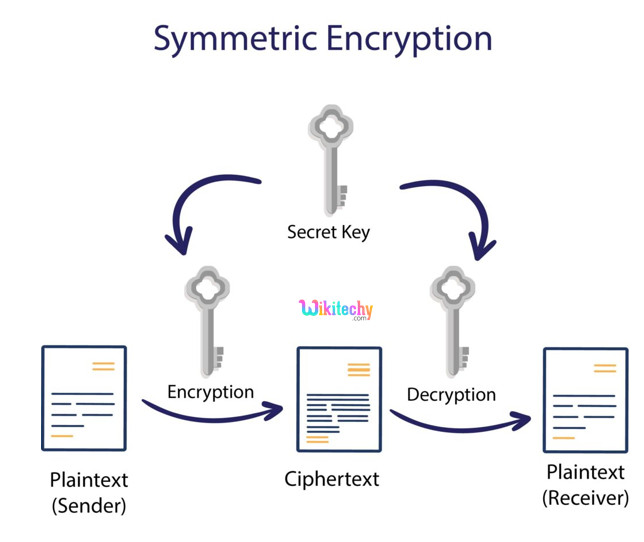
Secret Key Cryptography
- Secret Key Cryptography, or symmetric cryptography, makes use of a single key to encrypt information.
- Both encryption and decryption in symmetric cryptography use the identical key, making this the perfect form of cryptography.
- The cryptographic algorithm makes use of the key in a cipher to encrypt the information, and when the data have to be accessed again, someone entrusted with the secret key can decrypt the data.
- Secret Key Cryptography may be used on each in-transit and at-rest data, but is generally only used on at-rest data, as sending the secret to the recipient of the message can lead to compromise.
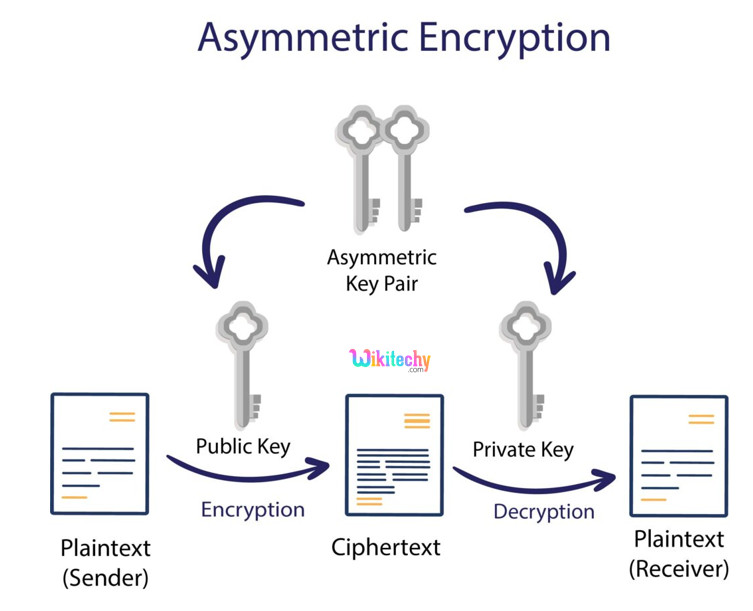
Public Key Cryptography
- Public Key Cryptography, or asymmetric cryptography, makes use of keys to encrypt data.
- It is used for encryption, while the alternative key can decrypts the message. Unlike symmetric cryptography, if one key is used to encrypt, that identical key can’t decrypt the message, rather the alternative key will be
- One key is saved private, and is known as the “private key”, while the alternative is shared publicly and may be used by anyone, hence it is called the “public key”.
- The mathematical relation of the keys is such that the private key can’t be derived from the public key, but the public key may be derived from the private.
- The private key should not be allotted and must remain with the owner The public key may be given to some other entity.
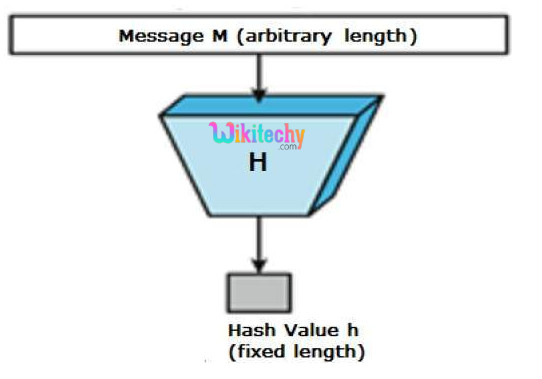
Hash Functions
- Hash functions are irreversible which secure the data, on the price of not being capable of recover the original
- Hashing is a way to convert a given string into a fixed length
- A good hashing algorithm will produce unique outputs for every input
- The simplest way to crack a hash is through attempting each input possible, untill you get the exact same hash.
- A hash may be used for hashing data (which includes passwords) and in certificates.