When many devices are on a shared network and need to communicate, who gets to talk first? Imagine being in a room full of people all trying to talk at once. It becomes a mess. Networks also struggle with this issue, and that’s where random access protocol comes into play.
What is Random Access Protocol?
Random access protocol is simply a type of multiple access protocol used in computer networks where devices transmit data as they have data to send, without order as there is no pre-scheduled turn.
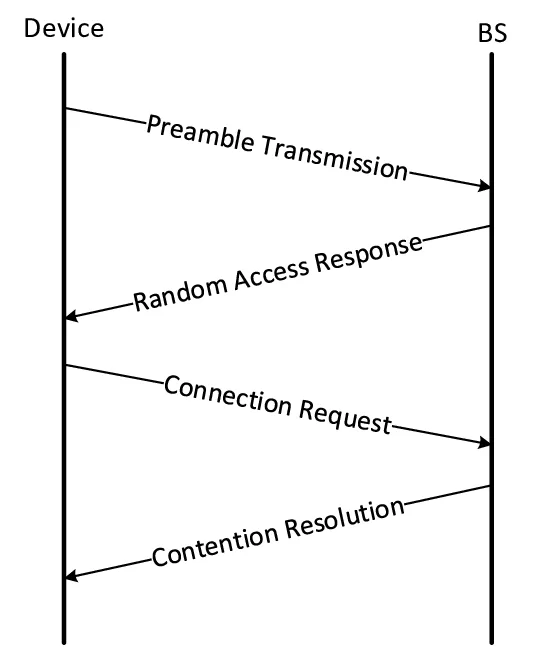
Because there is no turn-taking, there can be collisions (two devices sending the same data at the same time). When a collision occurs, there need to be protocols in place like ALOHA or CSMA (Carrier Sense Multiple Access) which will specify when the devices can transmit again for successfully communicating.
👉 And to put simply:
It’s like students in a classroom trying to answer questions all at once without raising their hands— sometimes they overlap, but eventually, everyone gets heard.
Examples of Random Access Protocols

- ALOHA Protocol – the original form of random access where devices randomly send data. This original form of random access has collision resolution, where if two devices send data at the same time, that is a collision, the devices wait a random amount of time before sending again.
- Slotted ALOHA – The initial inefficiencies were improved by taking time and breaking it into slots so that devices would always transmit at the start of each slot.
- CSMA (Carrier Sense Multiple Access) devices have the opportunity to listen to the channel before transmitting (attempt to avoid collisions).
- CSMA/CD (Collision Detection) – wired Ethernet implementation.
- CSMA/CA (Collision Avoidance) – Wireless, primarily Wi-Fi.
✅ Real-world Example: Your Wi-Fi at home is an example of CSMA/CA, in which multiple devices (e.g., laptop, phone, smart TV) are continually sending data and not resulting in non-stop chaos.
Controlled Access Protocol vs Random Access Protocol
Now, let’s compare random access protocol with controlled access protocol.
Controlled Access Protocol

- Devices will take turns according to some defined rule.
- Three methods for this are Polling, Token Passing and Reservation.
- An example of this access method is Token Ring networks. In this network type, a “token” is continually circulated. The only devices are able to transmit data when in possession of the token.
Random Access Protocol
- Devices can send data whenever they wish.
- Collisions will take place, but these devices use retransmission methods to resolve these collisions.
- An example of this would be Wi-Fi, which uses CSMA/CA.
👉 Analogy:
- Random Access = A crowded, busy street with no traffic lights (but driver negotiation).
- Controlled Access = An intersection with traffic lights (strict turn-taking).
Multiple Access Protocol: Where Random and Controlled Fit

The umbrella term here is multiple access protocol, which defines how multiple devices share a common communication channel.
There are three main categories:
- Random Access Protocol
- Examples: ALOHA, CSMA.
- Flexible, but prone to collisions.
- Controlled Access Protocol
- Examples: Polling, Token Passing.
- Less flexible, but orderly.
- Channelization Protocols
- Divide the channel into parts.
- Examples: TDMA (Time Division Multiple Access), FDMA (Frequency Division Multiple Access), CDMA (Code Division Multiple Access).
✅ Real-life Analogy:

- FDMA = Different radio stations on different frequencies.
- TDMA = TV commercials where advertisers “own” a time slot.
- CDMA = Everyone talking in different languages in the same room.
Why Random Access Protocol Still Matters Today
Even though controlled access sounds cleaner, random access is still widely used because:
- Flexibility: No need for “rigid” control.
- Scalability: Well-suited to large, dynamic networks (e.g. Wi-Fi Hotspots).
- Simplicity: Simpler to apply than incident scheduling.
For instance, the internet as we know it relies heavily on random access protocols for Ethernet (CSMA/CD) and Wi-Fi (CSMA/CA).
Pros and Cons
✅ Advantages of Random Access Protocol
- Simple and cheap.
- No central unit required.
- Efficient at low rates of traffic.
❌ Disadvantages
- Collisions increase due to increase traffic.
- Throughput decrease significantly under congestion.
- Not suitable for real-time or high-priority traffic.
Real-World Applications
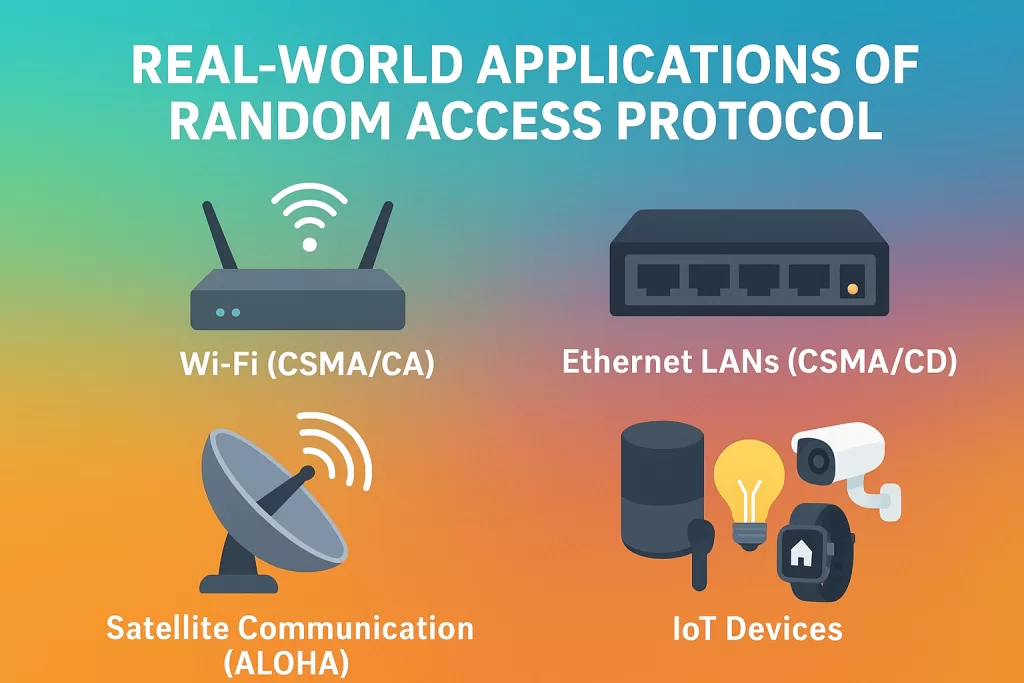
- Wi-Fi (CSMA/CA) – Typical home local area networks.
- Ethernet LANs (CSMA/CD) – Office-wired communications.
- Satellite Communication (ALOHA) – Early data transfer using satellites.
- IoT Devices – Billions of devices that are smart and can transmit data intermittently.
FAQs on Random Access Protocol
Q1. Why do networks need special rules for sharing the same channel?
👉 If there weren’t any rules, one device may interfere with another device causing a data collision and failure to communicate. Access methods specify how devices take turns using the channel, or compete to use a channel, and how they avoid interference.
Q2. Which method works better when many devices are on at the same time?
👉 Structured approaches usually work better than random approaches under high-traffic situations since structured approaches can help minimize congestion. Random approaches can still work, but they may introduce delays.
Q3. Are the same access methods used in wired and wireless networks?
👉 Not necessarily. Wired networks use one set of techniques, and wireless networks use a slightly different set of techniques because of interference and signal issues.
Q4. Can these methods be combined in modern systems?
👉 Yes. Many modern systems can blend different access methods—e.g., time slots and collision detection— to achieve a healthy balance of efficiency and reliability.
Q5. Where are these concepts used in everyday life?
👉 Home Wi-Fi, mobile networks, office LANs (local area networks), even satellite systems operate using one or more of these concepts to coordinate communication.
Conclusion
Random access is a critical component in networks, in turn allowing devices to communicate without following strict protocols and schedules. While controlled access protocols keep things in line, and multiple access protocols cover the big picture, random access is simply too important and is still granting us the benefits of Wi-Fi and Ethernet protocols today. With networks rapidly growing via IoT, 5G, etc., and the addition of autonomous devices, it is extremely valuable for cars, engineers, students, and technology enthusiasts to understand the three forms of communication and protocols associated with them.
👉 In other words:
- Random Access = the ultimate in flexibility, but can create collisions.
- Controlled Access = order in which to follow, but less flexibility.
- Multiple Access = the big umbrella that makes all networks possible.


