IOT Hacking
Ethical hacking tracks the hacking guidelines for effective system operation. While several factors contribute to its development, one of the most important is its availability of IoT hacking tools that make the job easier to handle. An ethical hacker is a security expert’s who legally hacks a computer to detect risks and illegal access.
Table Of Content
- What are IoT Ethical tools ?
- Why are IoT Ethical Hacking tools used ?
- IoT Hacking Tools
- 1. Wireshark
- Benefits of Wireshark Tool
- Nmap
- Benefits of Nmap
- Fiddler
- Benefits of Fiddler
- Metasploit
- Benefits of Metasploit
- 5. Maltego
- Benefits of Maltego
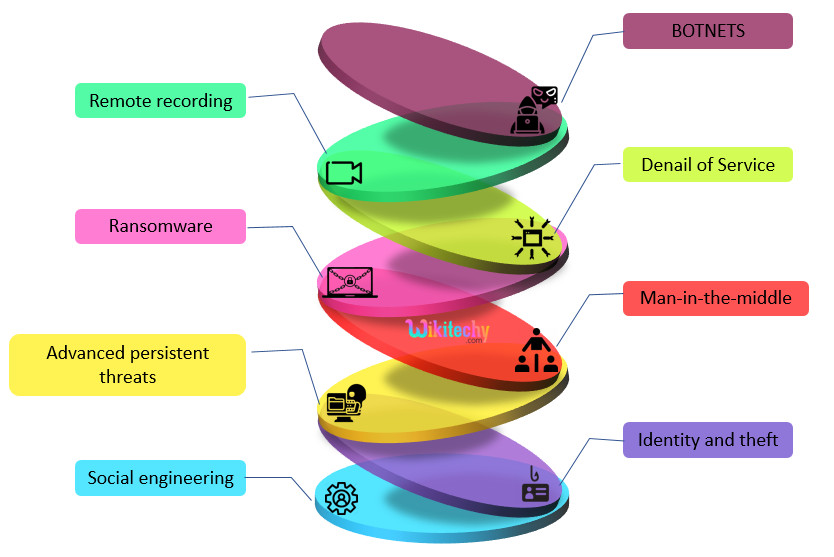
- Types of security threats to IoT
- Botnets
- Denial of service
- Man-in-the-Middle
- Identity and data theft
- Social engineering
- Advanced Persistent Threats
- Ransomware
- Remote recording
Every security expert must know all devices within the network, including the Internet of things (IoT), thoroughly in the core of ethical hacking. IoT hacking tools allow ethical hacking as they help to systematize the necessary steps. Ethical hackers can use them to perform certain features that help to detect device vulnerabilities.
What are IoT Ethical tools ?
Ethical hacking IoT tools help collect information, malicious behavior and payloads, password cracking, and a range of other activities. Hacking Tools are computer programs and scripts that help in detecting defects in web applications, computer systems and networks.
Why are IoT Ethical Hacking tools used ?
- Ethical hacking helps corporations keep their information and systems better.
- It is also the best way to improve the skills of an organization’s security professionals.
- It can be beneficial to make ethical hacking part of an organization’s security efforts.
IoT Hacking Tools
1. Wireshark
- Wireshark is a network packet analyzer that permits you to analyze network traffic in real-time.
- It is an open-source program considered by ethical hackers to be one of the most critical network security tools.
- In brief, you can capture and view information through your network with Wireshark.
- This tool is used if there is a problem with their hacking tools by expert penetration testing companies. In the forensics industry, Wireshark or similar devices are generally used.
- It is usually used to resolve the network’s performance, detect unusual traffic, misconfigured programming, and protocol problems.
- Ethical hackers will use network protocol analyzers to gain a detailed kind of a target network.
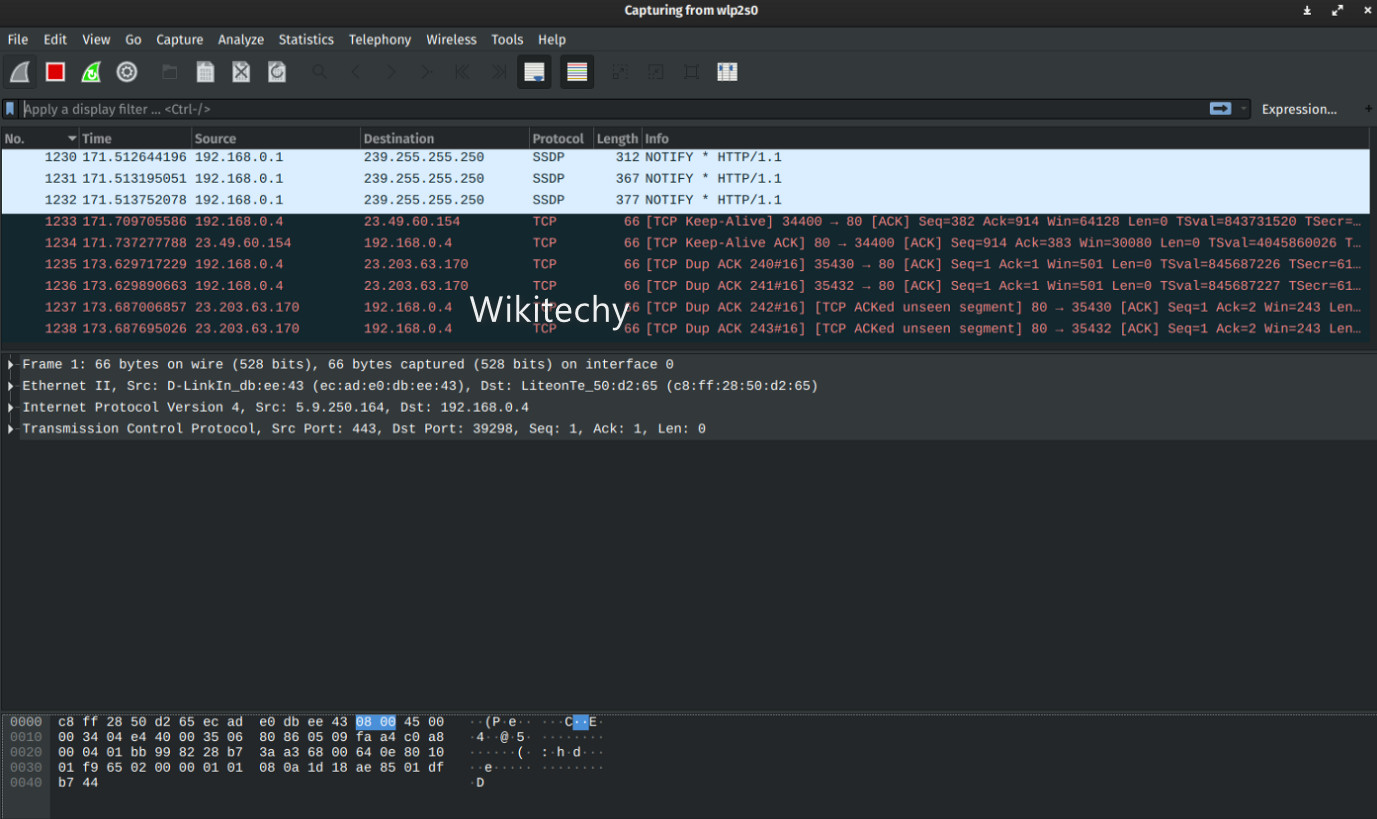
Benefits of Wireshark Tool:
- It is available for Windows and Unix platform.
- Detect traffic issues you have sent and received.
- Decoding traffic from another person.
- It can see complete details about packets inside a network and is not registered.
Nmap
- Network Mapper ( Nmap ) is a Open source scanning tool used in network discovery, and At the time of scanning, it sends crafted packets to determine the devices connected to the network.
- It then gives data to the operating system they are running to analyze the responses.
- Nmap is particularly developed for enterprise-scale networks to scan Hundreds of devices.
- Nmap helps network administrators to detect vulnerabilities.
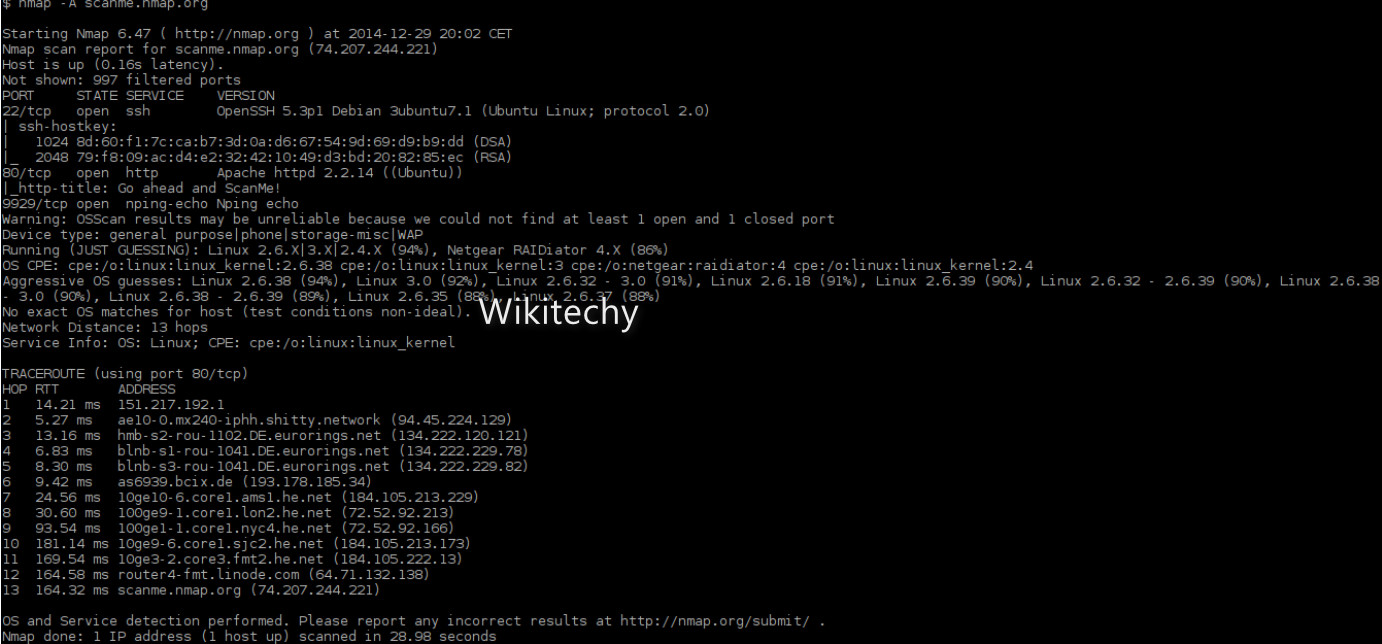
Benefits of Nmap:
- Interaction with the target host is possible using the Nmap scripting engine.
- It is used in checking the network for detecting the new servers.
Fiddler
- A Fiddler is an open-source web proxy tool that works with any platform or browser.
- It has many features to help a pen-testing device.
- It allows users to correct the web traffic on any system.
- Fiddler tool is mostly used to interrupt and decrypt HTTPS traffic from a pen testing point of view.
- Specialists use it to debug to see that the system is transfer HTTP requests to a website or service.
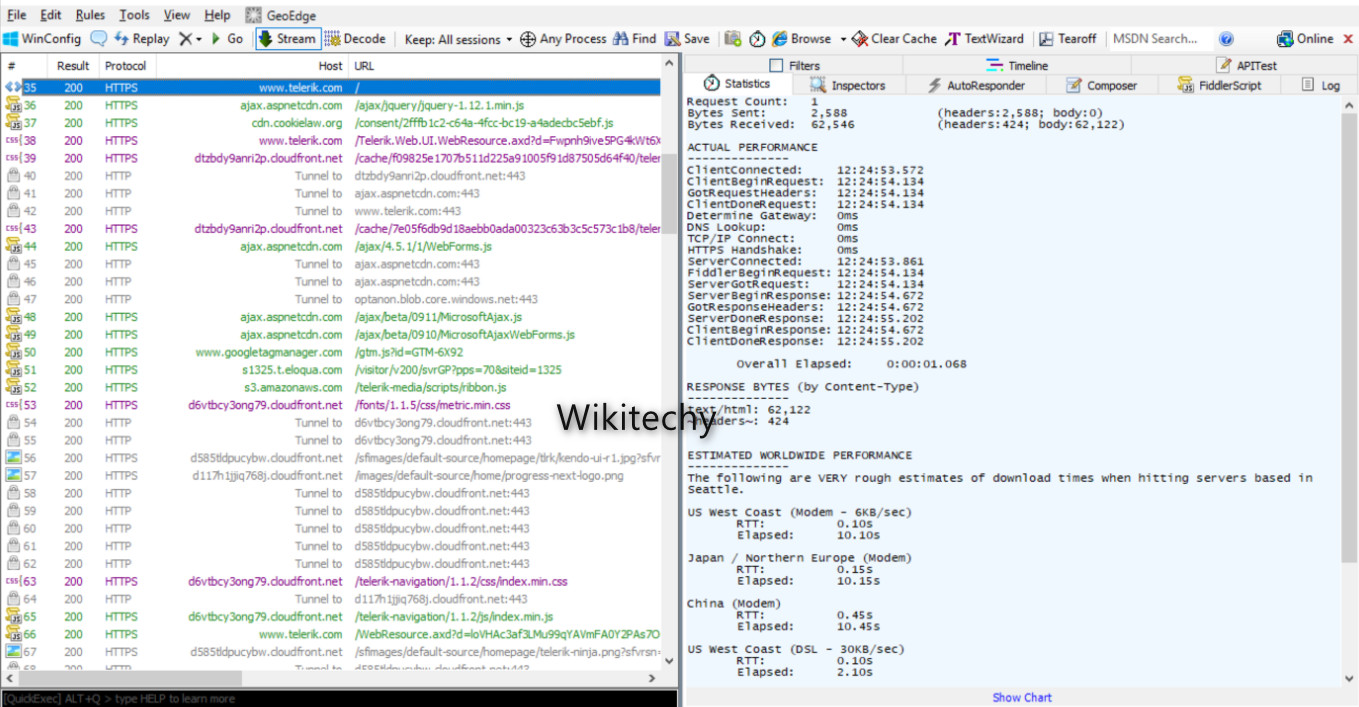
Benefits of Fiddler:
- Works with nearly every HTTP client.
- Can stop customer traffic on non-Windows platforms also.
Metasploit
- It is a security tool that gives software security information and improves penetration testing.
- It is an open-source penetration tool used to test weaknesses in the computer and gain access to the computer remotely and secure them from hacking.
- Metasploit is also used in threat hunting by discovering the vulnerabilities and reporting them, and systematic bugs are fixed with information gained.
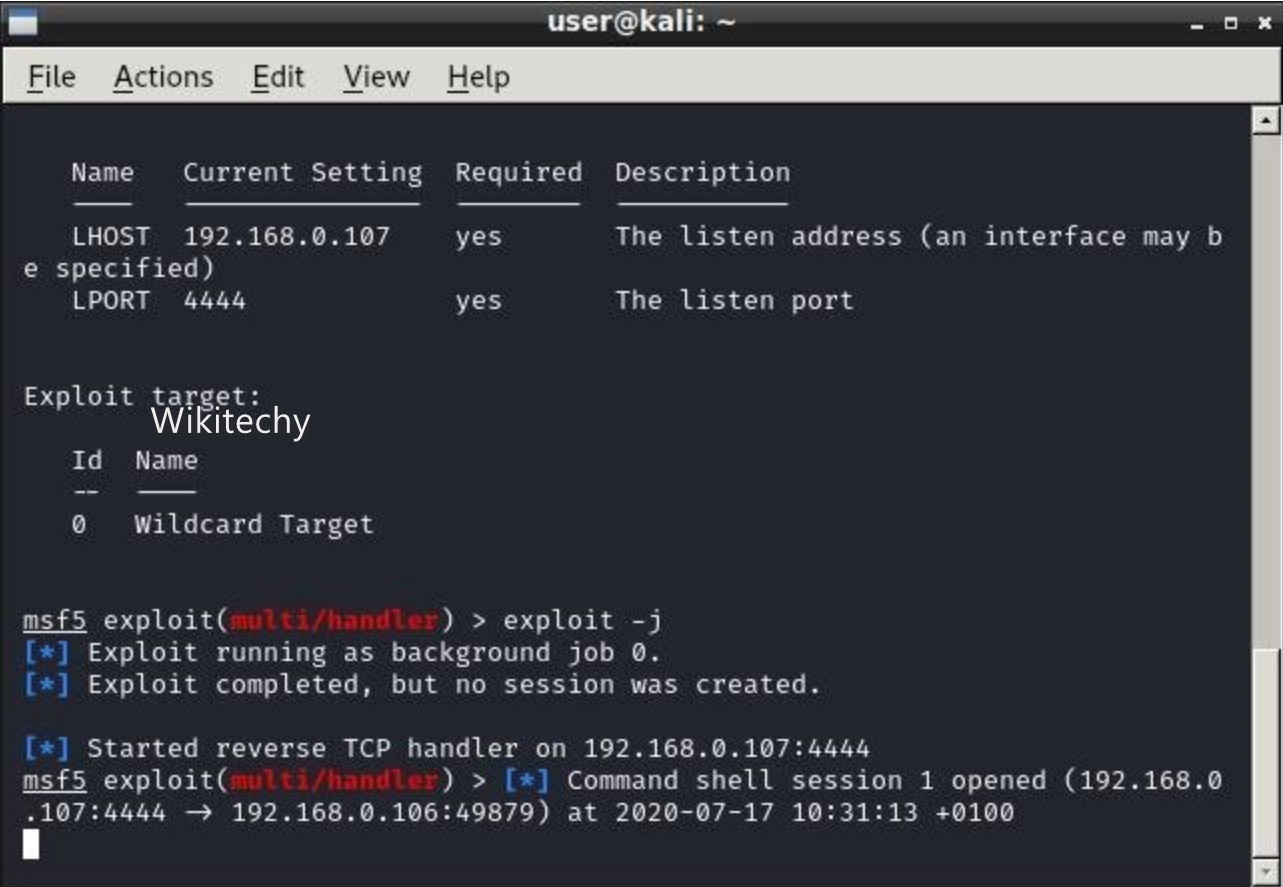
Benefits of Metasploit:
- It is open source and easy to use for free.
- It allows the users to access its source code and add their modified modules.
5. Maltego
- Maltego is an open-source tool; it has a complete method to collect and connect the information to investigative tasks through Open-Source intelligence and graphical relation analysis in real-time.
- It focuses on providing a library of transforms to find data from open sources and imagine it in a graph format that can be used for connection analysis and data mining.
- Maltego is a collective data mining tool that offers link analysis graphs.
- The device is used in online investigations to learn connections from different online sources.
- It probes the Internet, makes sense of the data and helps connect the results.
Benefits of Maltego:
- To show the complexity and severity of single failure points.
- It denotes information in a simple and easy-to-understand method.
Types of security threats to IoT
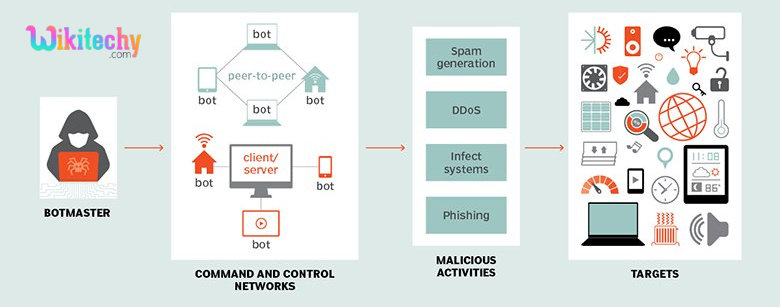
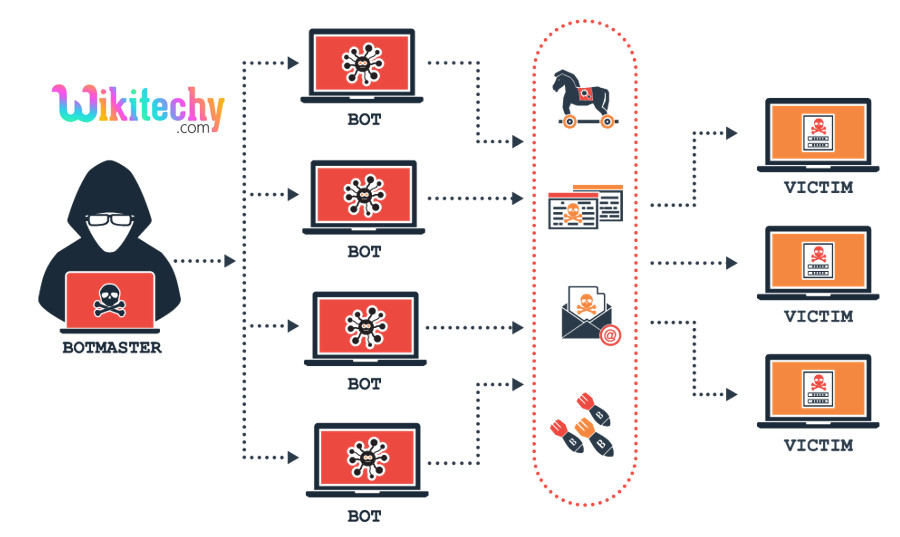
Botnets
- A botnet is a community that mixes various systems together to remotely take manage over a victim’s device and distribute malware.
- Cybercriminals manage botnets the usage of Command-and-Control-Servers to steal private data, gather online-banking data, and execute cyber attacks like DDoS and phishing.
- Cybercriminals can make use of botnets to attack IoT devices which can be related to several different devices along with laptops, desktops, and smartphones.
- Mirai botnet has displayed how dangerous IoT protection threats can be. The Mirai botnet has infected an anticipated 2.5 million devices, consisting of routers, printers, and clever cameras.
- Attackers used the botnet to release disbursed denial of service attacks on several IoT devices.
- After witnessing the effect of Mirai, several cybercriminals have developed a couple of superior IoT botnets.
- These botnets can release sophisticated cyber attack towards vulnerable IoT devices.
Denial of service
- A denial-of-service (DoS) attack intentionally attempts to reason a ability overload in the target device through sending a couple of requests.
- Unlike phishing and brute-force attack, attackers who implement denial-of-service don’t goal to thieve essential data.
- However, DoS may be used to slow down or disable a service to harm the recognition of a business.
- For instance, an airline this is attacked the usage of denial-of-service could be not able to method requests for reserving a brand new ticket, checking flight status, and canceling a ticket. In such instances, clients may also transfer to different airways for air travel.
- Similarly, IoT safety threats including denial-of-service attacks can break the recognition of corporations and affect their revenue.
Man-in-the-Middle
- In a Man-in-the-Middle (MiTM) attack, a hacker breaches the communication channel between individual systems in a try to intercept messages among them.
- Attackers benefit manage over their communication and send illegitimate messages to participating systems. Such attack may be used to hack IoT devices such as clever refrigerators and independent
- Man-in-the-middle attack may be used to attack several IoT devices as they share information in real-time.
- With MiTM, attackers can intercept communications between a couple of IoT devices, main to critical malfunction.
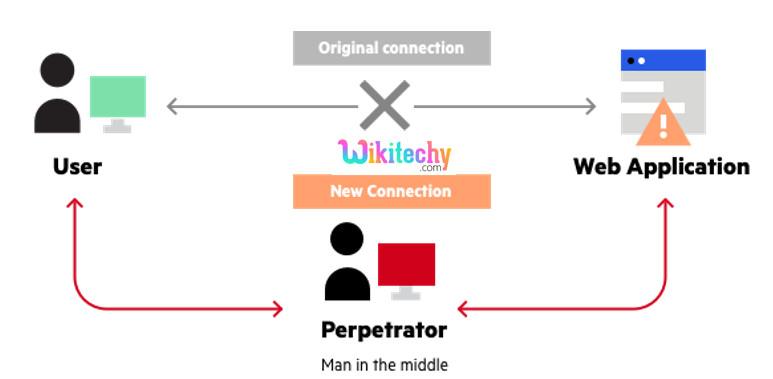
Identity and data theft
- Multiple information breaches made headlines in 2018 for compromising the information of millions of people.
- Confidential information which include private details, credit and debit card credentials, and e-mail addresses have been stolen in those information.
- Hackers can now attack IoT devices which include clever watches, clever meters, and clever home devices to benefit extra information about several customers and organizations.
- By collecting such information, attackers can execute greater sophisticated and specific identification
- Attackers also can exploit vulnerabilities in IoT gadgets which are linked to different devices and organization systems.
- For instance, hackers can attack a vulnerable IoT sensor in an organization and benefit access to their business
- In this manner, attackers can infiltrate a couple of organization systems and gain sensitive business information.
- Hence, IoT security threats can supply rise to information breaches in a couple of businesses.
Social engineering
- Hackers use social engineering to control human beings into giving up their sensitive data such as passwords and bank details.
- Alternatively, cybercriminals may use social engineering to get entry to a system for installing malicious software.
- Usually, social engineering attacks are completed the use of phishing emails, in which an attacker has to develop convincing emails to control human beings.
- However, social engineering attacks may be less difficult to execute in case of IoT devices.
- IoT devices, especially wearables, collect huge volumes of individually identifiable data (PII) to develop a customized experience for their customers.
- Such devices additionally make use of private data of customers to supply consumer-pleasant services, for example, ordering products online with voice control.
- However, PII may be accessed through attackers to advantage personal data including bank details, buy history, and home address.
- Such data can permit a cybercriminal to execute a sophisticated social engineering attacks that targets a person and their family and friends the use of vulnerable IoT networks.
- In this manner, IoT protection threats including social engineering may be used to advantage illegal access to user data.
Advanced Persistent Threats
- Advanced persistent threats (APTs) is a targeted cyber attack, where an intruder profits illegal access to a network and remains undetected for an extended duration of time.
- Attackers goal to monitor network activity and steal important information using persistent threats.
- Such cyber attacks are hard to prevent, detect, or mitigate.
- With the arrival of IoT, huge volumes of crucial information are effortlessly transferred among several devices.
- A cybercriminal can goal those IoT devices to gain access to private or personal networks.
- With this approach, cybercriminals can steal personal information.
Ransomware
- Ransomware attacks have become one of the most cyber threats.
- In this attack, a hacker makes use of malware to encrypt information that can be required for business operations.
- An attacker will decrypt important data only after receiving a ransom.
- Ransomware may be one of the most sophisticated IoT security threats.
Remote recording
- Documents launched through WikiLeaks have shown that intelligence organizations know about the existence of zero-day exploits in IoT devices, smartphones, and laptops.
- These files suggest that safety organizations had been making plans to document public conversations secretly.
- These zero-day exploits also can be utilized by cybercriminals to document conversations of IoT users.
- For instance, a hacker can attack a camera in an organization and record video photos of normal business activities.
- With this approach, cybercriminals can collect personal business information secretely.

