Cyber Attack - What is a Cyber Attack - Cyber Security Tutorial
What is Cyber Attack ?
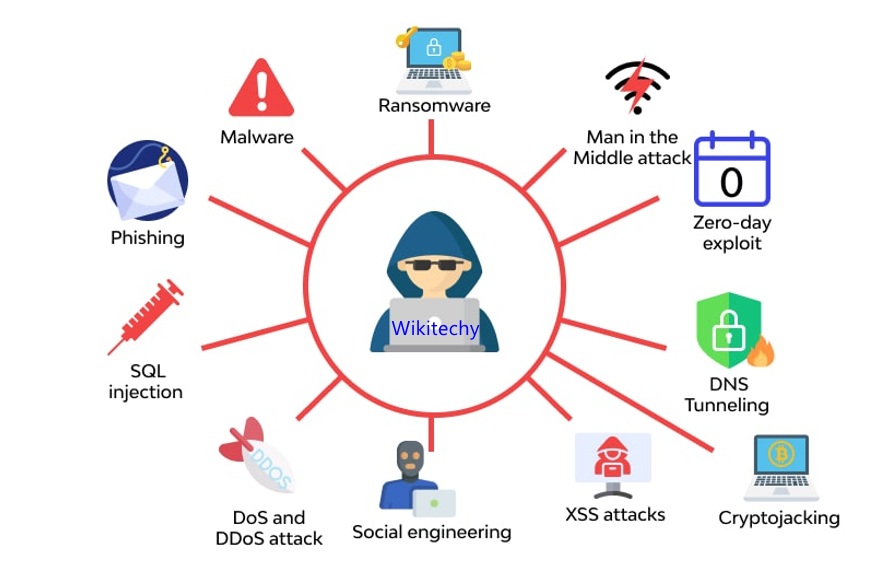
- A Cyber Attack is any attempt to gain unauthorized access to a computer, computing system or computer network with the intent to cause damage.
- Cyber attacks aim to :
- Disable,
- Disrupt,
- Destroy or Control Computer Systems
- Alter,
- Block,
- Delete
- Manipulate or steal the data held within these systems.
- Any individual or group can launch a Cyber Attack from anywhere by using one or more various Attack strategies.
- People who carry out Cyber Attacks are generally regarded as Cyber Criminals
- Government-sponsored groups of computer experts also launch Cyber Attacks. They're identified as nation-state attackers
Who is behind Cyber Attacks ?
- Criminal organizations, state actors and private persons can launch cyberattacks against enterprises. One way to classify cyberattack risks is by outsider versus insider threats.
Outsider threats
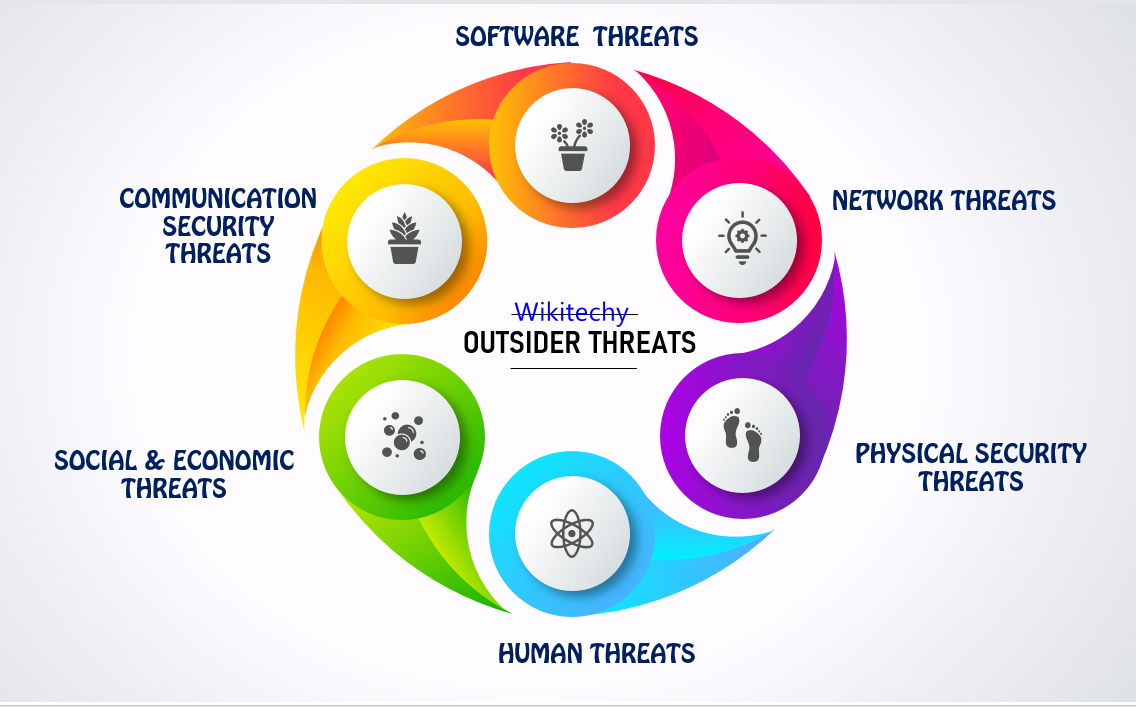
- External cyber threats include
- Organized criminals or criminal groups
- Professional hackers, like state-sponsored actors
- Amateur hackers, like hacktivists
Insider threats
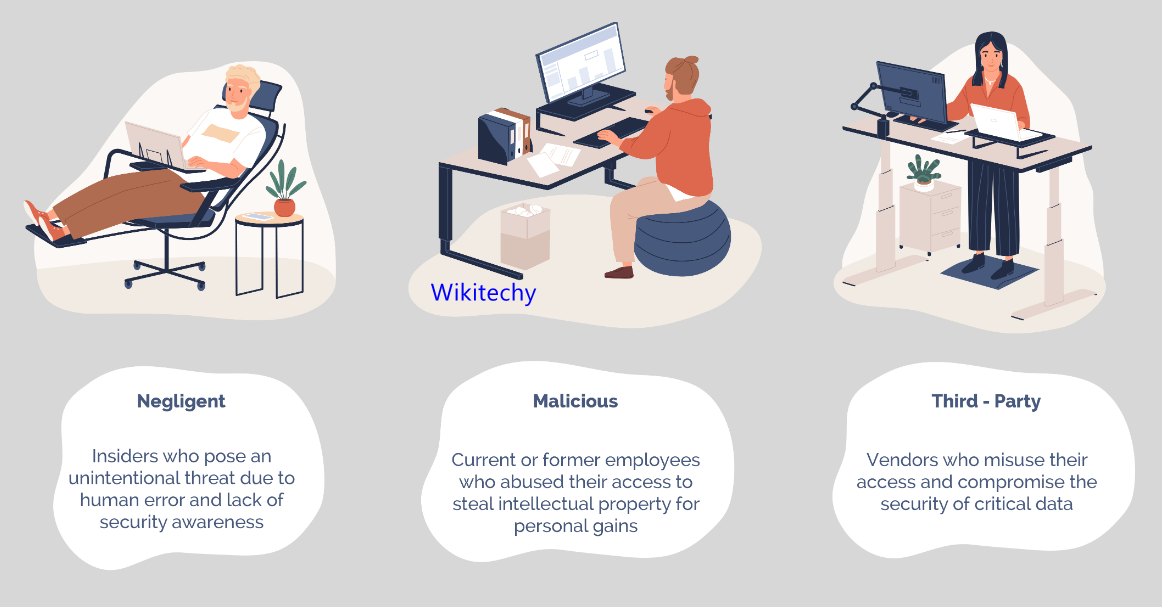
- Insider threats are users who have authorized and legitimate access to a company's assets and abuse them either deliberately or accidentally. They include:
- Employees careless of security policies and procedures
- Disgruntled current or former employees
- Business partners, clients, contractors or suppliers with system access
How do cyber attacks work ?
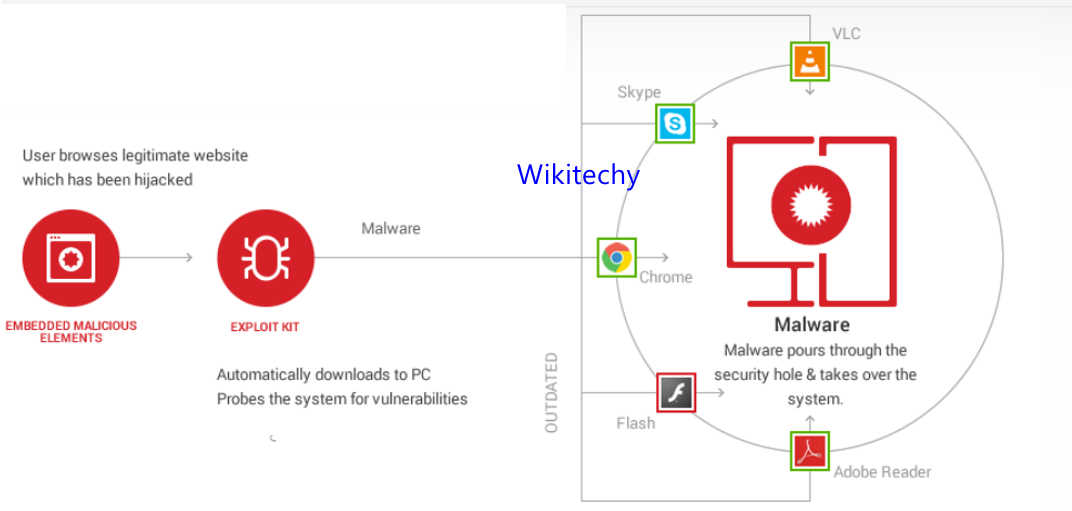
- Threat actors use various techniques to launch cyber attacks, depending in large part on whether they're attacking a targeted or an untargeted entity.
Untargeted Attack
- Where the bad actors are trying to break into as many devices or systems as possible,
- They generally look for vulnerabilities in software code that will enable them to gain access without being detected or blocked.
- They might employ a Phishing Attack, emailing large numbers of people with Socially engineered messages crafted to entice recipients to click a link that will download malicious code.
Targeted Attack
- The threat actors are going after a specific organization, and the methods used vary depending on the attack's objectives.
- Hackers also use spear-phishing campaigns in a targeted attack, crafting emails to specific individuals
- who, if they click included links, would download malicious software designed to subvert the organization's technology or the sensitive data it holds.
