- Ethical hacking involves an authorized attempt to gain unauthorized access to a Computer System, Application, or Data.
- Carrying out an ethical hack involves duplicating strategies and actions of malicious attackers.
- This practice helps to identify security vulnerabilities which can then be resolved before a malicious attacker has the opportunity to exploit them.
Ethical Hacking Protocols
Stay legal
- Obtain proper approval before accessing and performing a Security Assessment
Define the scope
- Determine the scope of the assessment so that the ethical hacker’s work remains legal and within the organization’s approved boundaries.
Report vulnerabilities
- Notify the organization of all vulnerabilities discovered during the assessment.
- Provide remediation advice for resolving these vulnerabilities.
Respect data sensitivity
- Depending on the data sensitivity, ethical hackers may have to agree to a non-disclosure agreement,
- In addition to other terms and conditions required by the assessed organization.
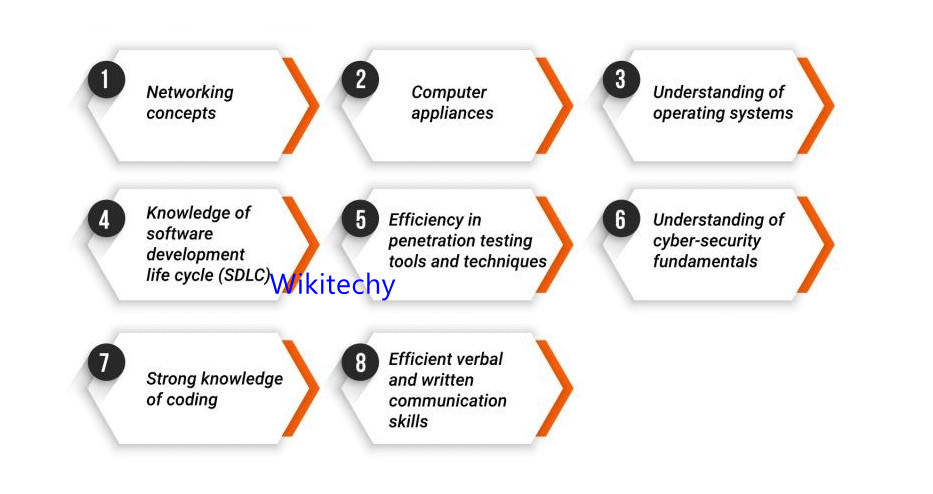
Skills Required to Become a Ethical Hacker
Networking concepts
- How two devices communicates
- How protocols works
- Encrypted Networks Workflow
- Wireless communictions
Basic programming Knowledges
- How a piece of code works
- How viruses is written in coding prespective
- How to decode a piece of code
- How an application works code wise
Linux Administration
- Linux Management
- Linux User and Network Management
- Different Linux Distributions
- Linux Command Line Utility
- Bash Commands
- Knowledge in Shell Scripting
Understanding of operating systems
- What is a OS
- Different OS Workflow
- OS Architecture
- OS Core Concepts
- OS Functions
- Hands on Experience in Different OS
Latest Cyber Security Threats
- Client Side Threats
- Latest Vulnerablitiy Patches
- How Certain Attack Works
- Server Side Threats
- Wireless Attacks
Strong knowledge of coding
- To UnderStand Programs
- For Writing Secure Codes
- To ExamineVulnerablitiy
- For Reverse Engineering
- Malware Analysis
UP NEXT IN Cyber Security