Enumeration in Ethical Hacking
Enumeration is one of the phases of Penetration Testing or Ethical Hacking. It is a process of gaining complete access to the system by cooperating the vulnerabilities identified in the first two phases. The Scanning stage only supports to find the vulnerabilities to a certain level, but Enumeration helps us learn the whole details such as users, groups and even system level details – routing tables. This phase of the Ethical hacking is to gain end-to-end knowledge of what will be tested in the target environment. Tools are installed to gain complete control over the system.
Types of information enumerated by intruders
- Network Resource and shares
- Users and Groups
- Routing tables
- Auditing and Service settings
- Machine names
- Applications and banners
- SNMP and DNS details
Techniques for Enumeration
- Extract user names using SNMP
- Extract user groups from Windows
- Brute Force Active Directory
- Extract information using DNS Zone transfer
- Extracting user names using email ID’s
- Extract information using the default password
Significance of Enumeration
Enumeration is the feature of Ethical hacking. The metrics, outcomes, results are used directly in testing the system in the next steps of penetration testing.
Enumeration helps us to decrypt the full information – Hostnames, IP tables, SNMP and DNS, Application, Banners, Audit configurations and service settings. Enumeration meaning is that it systematically collects details. This allows pentesters to entirely examine the systems. The pentesters collect information about the weak links in the enumeration phase of ethical hacking. It helps in finding the attack Vectors and threats.
Enumeration Classification
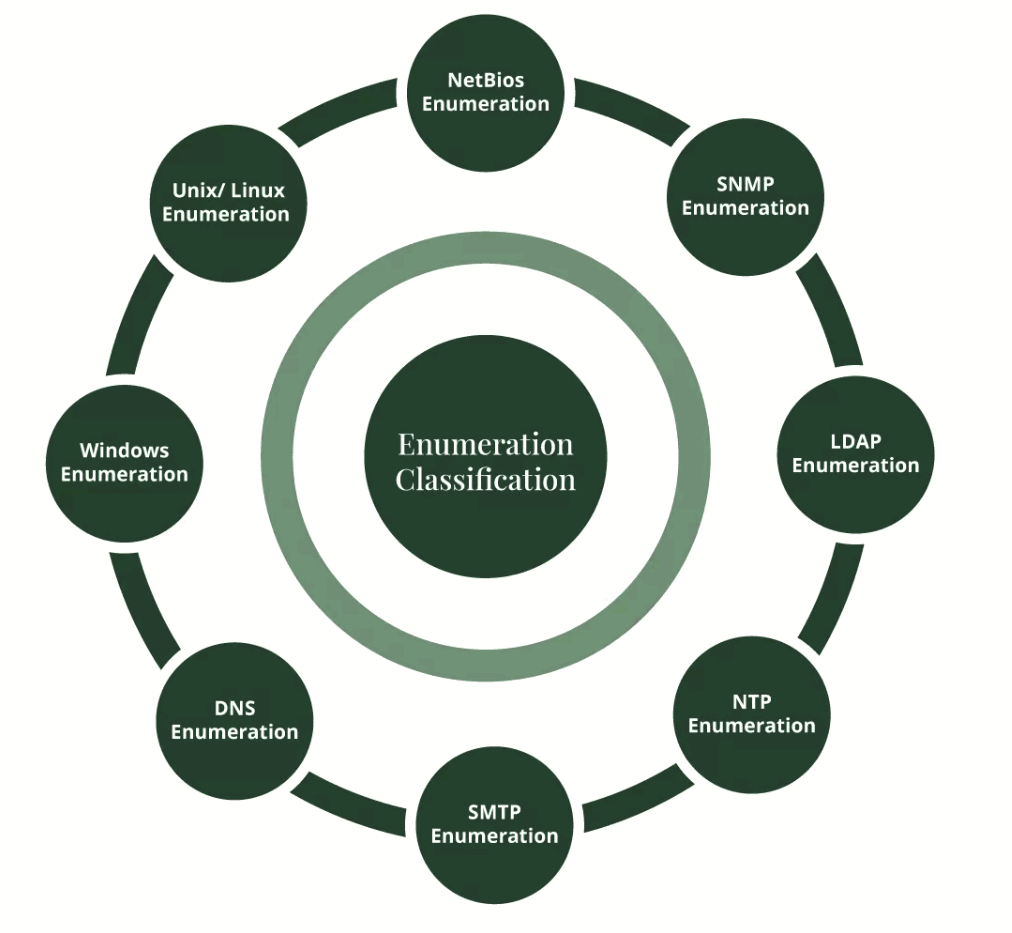
What are the goals of the Enumeration ?
- To map the end-to-end details that we need to check after the enumeration step
- The ways to execute the attacks in the future phases
- Identify all the information we need to do the implementation in future testing
- Compile a list of devices with configuration for testing
- Complete the network map to confirm the steps for testing
- Compile the list of people who support the testing
- Collect even unrelated information that might still be important in the future
Process of Enumeration
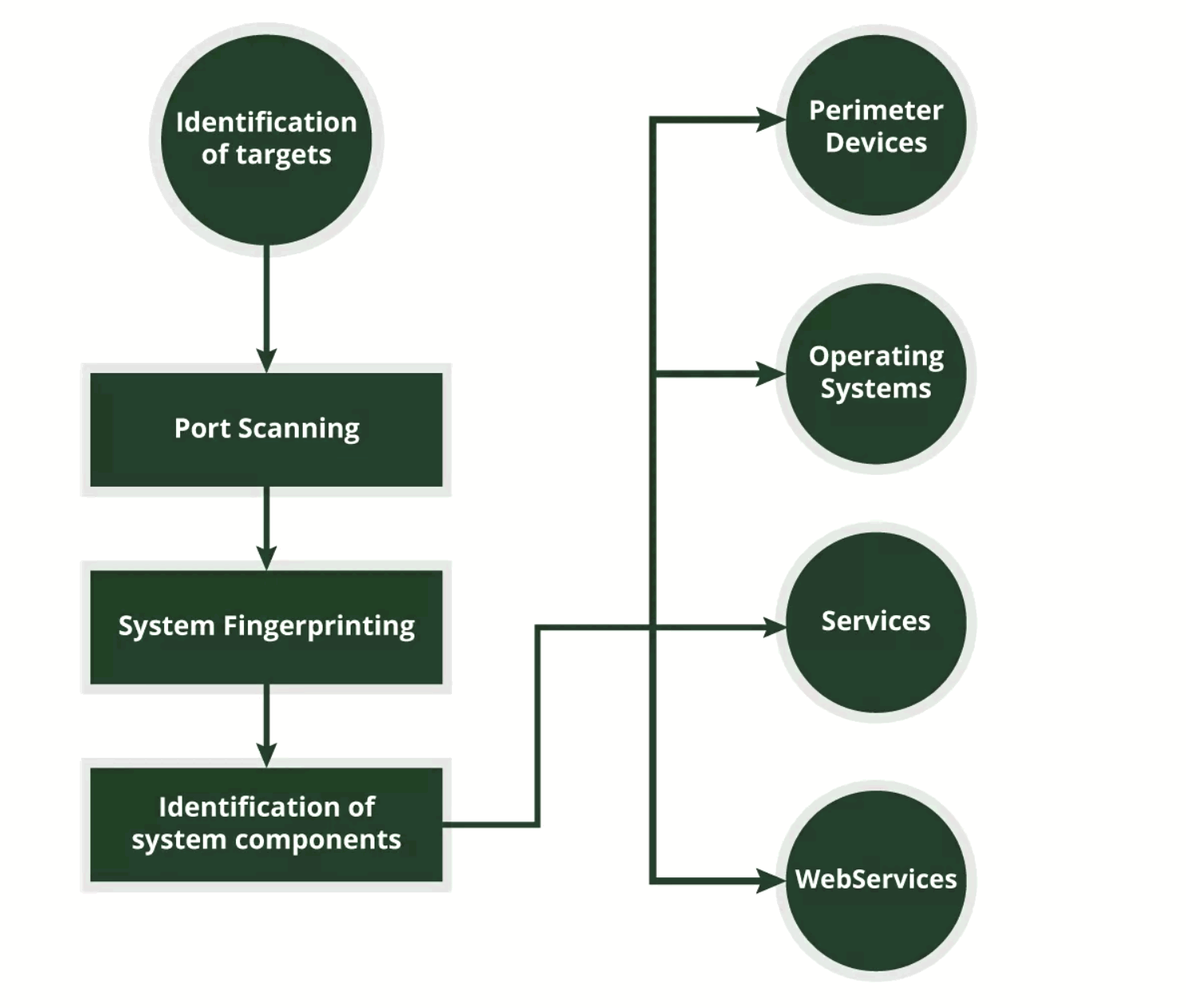
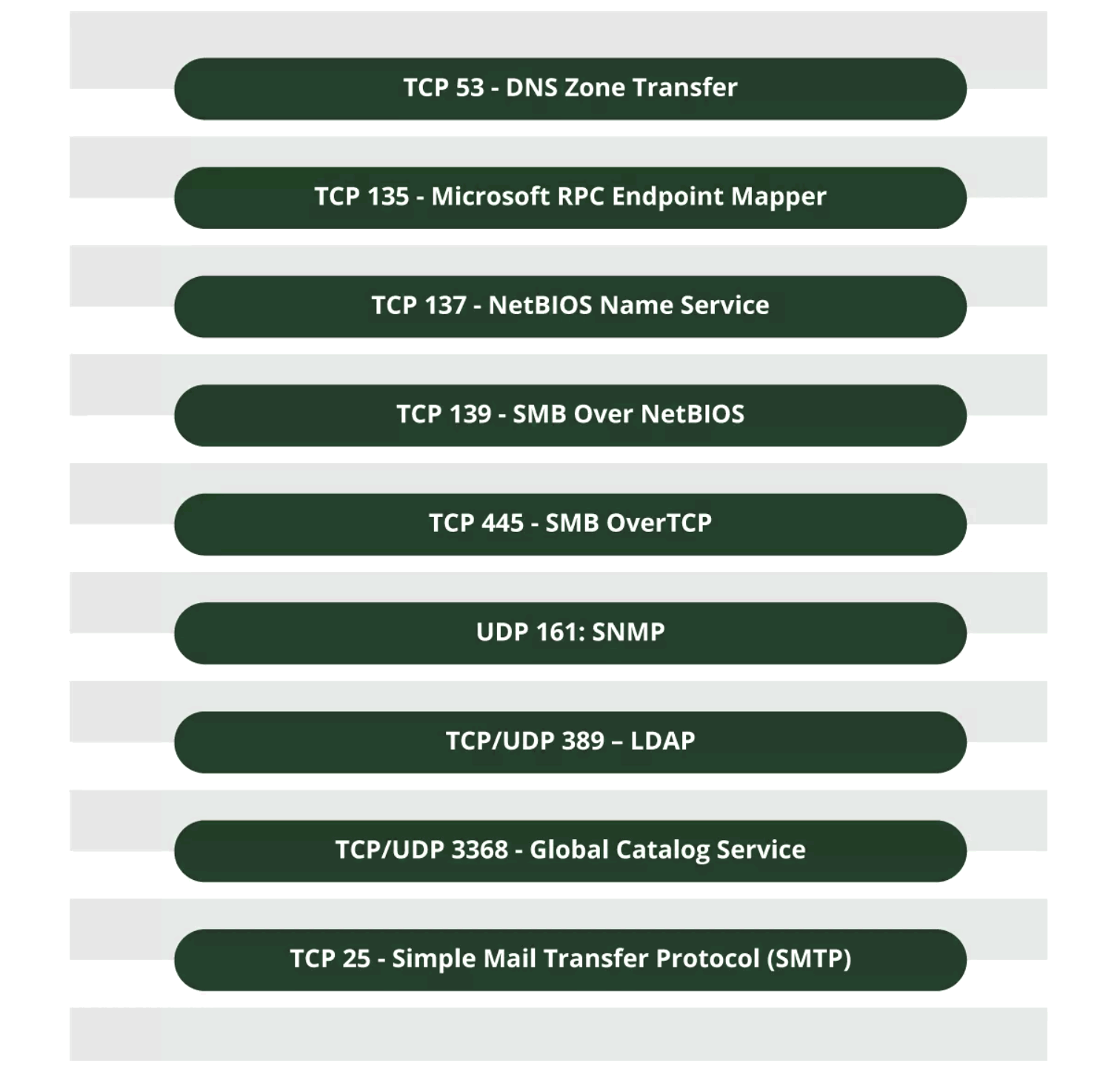
Services and Port to Enumerate
Tools supporting Enumeration
| Tool | Use | Service |
| Nmap | Network mapper | To determine port and service information on a target
|
| Nessus | Service and vulnerability scanner. | Identify vulnerable services |
| WPScan | WordPress vulnerability scanner | Identify vulnerable WordPress applications |
| Searchsploit | CLI tool for exploit.db for exploits | To look up exploits for services. |
| GoBuster | Web directory brute forcer | Discover directories on web servers. |
| Dig | Domain Information Groper | Used to query DNS servers |
| Nmblookup | SMB share lookup. | Find any open and exposed SMB shares |
| Dnsenum | Enumerate DNS information |
Port – Scanning Enumeration
- Port scanning is the common form of enumeration. This is used to learn the many services which can exploit the systems. This includes all the systems that are connected to LAN or accessing the network through the modem which runs the services. We can find out what services are running, who are the owners of these services and if any of them needs a separate verification.
NetBIOS (Network Basic Input Output System) Enumeration
- It helps in computer communication with LAN for sharing files and printers.
- They are mainly used for finding the network devices.
- The naming is 16 characters – 15 characters for the device and the 16th denotes the service it runs.
- Attackers use the NetBIOS for scanning the list of computers per domain, policies and passwords and other shares in the network.
- Tools used in Netbios are Nbtstat, superscan, Net View, Hyena