Scanning is a set of procedures for finding live hosts, ports, and services, discovering Operating system and architecture of target system, Finding vulnerabilities and threats in the network.
Scanning refers to collecting more information using complex and aggressive reconnaissance techniques.
Scanning is of three types:
- Network Scanning
- Port Scanning
- Vulnerability Scanning
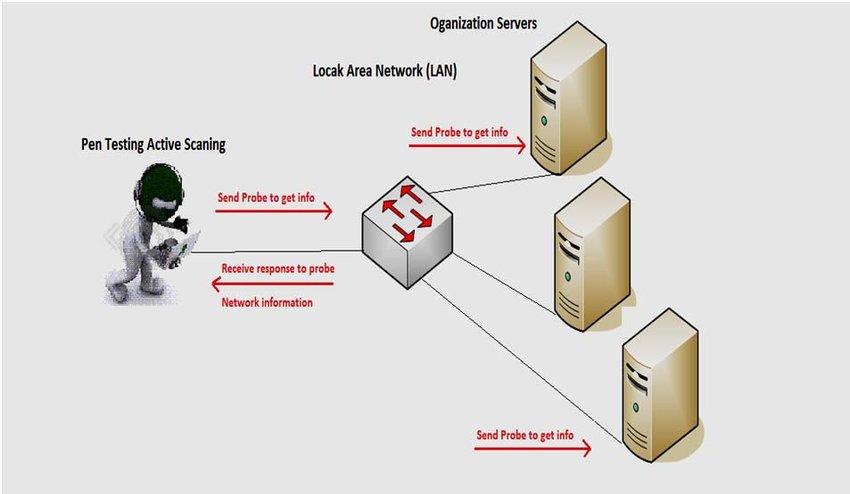
Network Scanning
- Network scanning is used to create a profile of the target organization.
- The objectives of Network Scanning,
- To learn live hosts/computer, IP address , and open ports of the victim.
- To learn services that are running on a host computer.
- To determine the Operating System and system architecture of the target.
- To realize and deal with vulnerabilities in Live hosts.

Scanning Methodologies
- Pen-testers and Hackers check for Live systems.
- Check for open ports (This method is called Port Scanning)
- Scanning beyond IDS (Intrusion Detection System)
- Banner Grabbing: Is the way for obtaining information regarding the targeted system on a network and services running on its open ports. Telnet and ID Serve are the tools used mainly to perform a Banner-grabbing attack. This information may be used by intruders/hackers to show the lists of applicable exploits.
- Scan for vulnerability
- Prepare Proxies
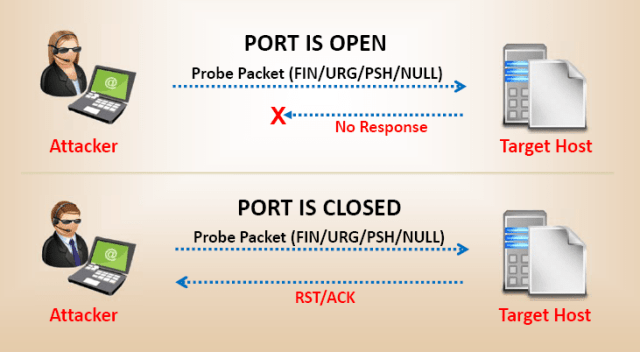
Port Scanning
It is a conventional technique used by penetration testers and hackers to search for open doors from which hackers can access any organization’s system. In this scan, hackers want to find out those live hosts, firewalls installed, operating systems used, different devices attached to the system, and the targeted organization’s topology. Once the Hacker makes the victim organization’s IP address by scanning TCP and UDP ports, the Hacker maps this organization’s network under his/her grab. Amap is a tool to perform port scanning.
Vulnerability Scanning
It is the proactive identification of the system’s vulnerabilities within a network in an automatic manner to control whether the system can be exploited or threatened. In this case, the computer should have to be connected to the internet.
Tools and Steps Used :
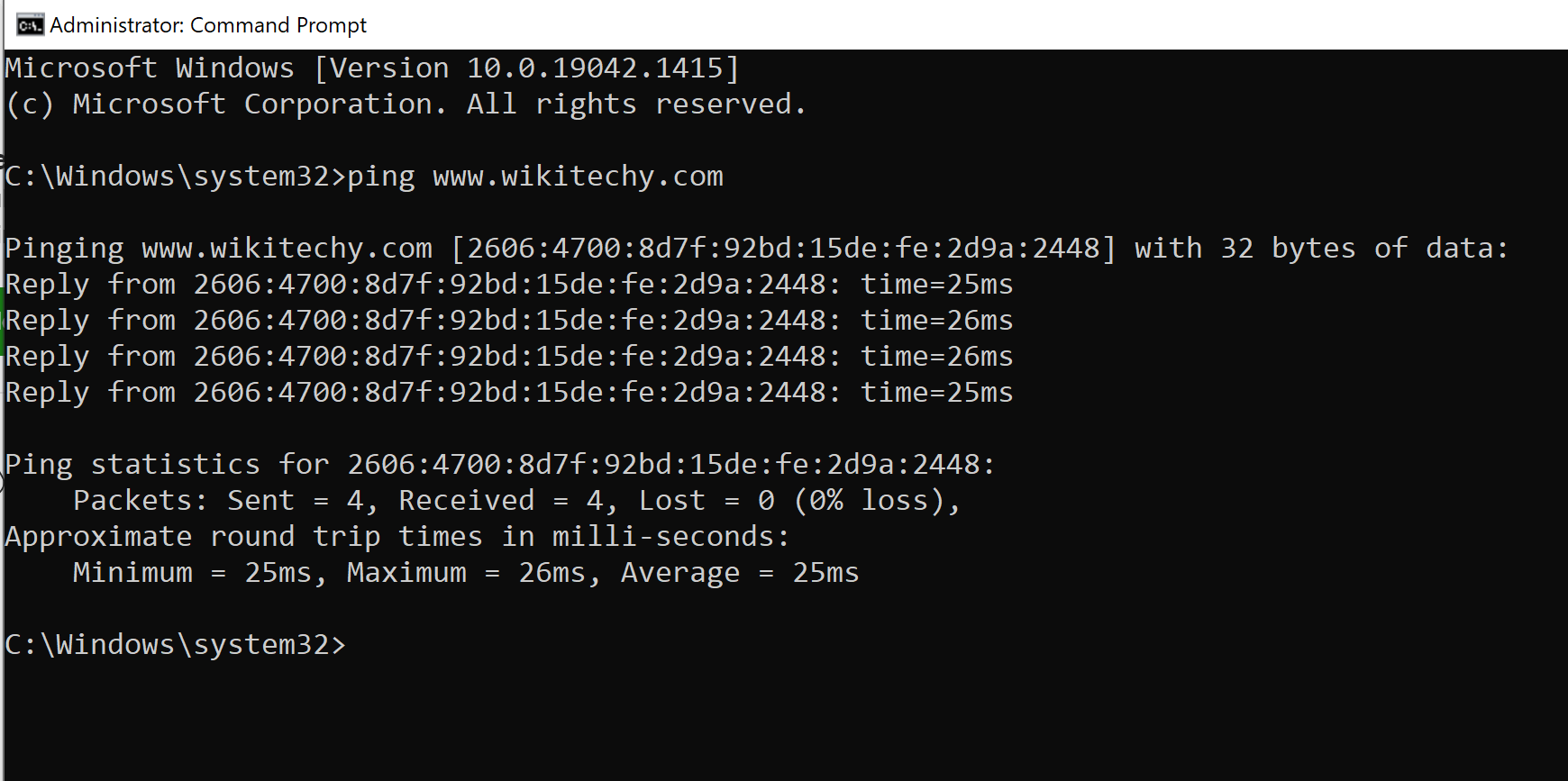
If a hacker needs to execute ICMP (Internet Control Message Protocol) scanning, it can be done manually. The steps are:
- Open Windows OS
- Press Win+R (Run) buttons in combination
- In the Run, type- cmd
- Type the command: ping IP Address or type: ping DomainName
Tools that can be used to scan networks and ports are:
Nmap:
- Nmap is a Network scanning tool that is used to extract information such as live hosts on the network, services, type of packet filters/firewalls, operating systems, and OS versions.
Angry IP Scanner:
- Scans for systems available in a given input range.
Hping2/Hping3:
- It is a command-line packet crafting and network scanning tools used for TCP/IP protocols.
Superscan:
- It is very powerful tool developed by Mcafee, which is a TCP port scanner, also used for pinging.
ZenMap:
- It is another powerful Graphical user interface (GUI) tool to detect the type of OS, OS version, ping sweep, port scanning, etc.
Net Scan Tool Suite Pack:
It is a collection of different types of tools that can perform a port scan, flooding, webrippers, mass emailers;
Wireshark and Omnipeak are two powerful and famous tools that listen to network traffic and act as network analyzers.
Names of other PCs tools are Advanced Port Scanner, Net Tools, MegaPing, CurrPorts, PRTG Network Monitor, SoftPerfect Network Scanner, Network Inventory Explorer, etc.